Battle vulnerabilities and strong-arm security incidents

According to a survey from Ponemon Institute[i], almost half of businesses have had a security breach in the last two years while the costs of a data breach were $3.9M, involving as many as 10,000 records. With this number, keep in mind that publicized breaches are just the tip of the iceberg. But it gets really interesting when you start looking for the cause. As much as 42% of all breaches are related to software vulnerabilities. The shocking part is that 34% of breach victims knew they were vulnerable. But then, did the company have vulnerability patches at hand? Well, yes! A staggering 57% of breaches could have been prevented by a patch that was already available. So, what’s going wrong here?
Ineffectiveness of current vulnerability applications
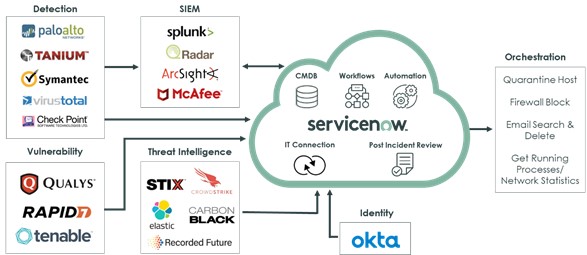
Most organizations have invested in dozens of security products for different purposes like detection, prevention and protection. Some are end-point security products or firewalls that customers have been using for years. Others are professional security tools used by security specialists only. Some even have vulnerability scanners, SIEMs and threat intelligence products. While these security products do a nice job in protecting the business and detecting potential security incidents, they create a huge number of alerts–sometimes hundreds or even thousands a day! Without automation, categorizing, prioritizing and filtering out critical alerts is a very complex and time-consuming process.
More research from Ponemon Institute reveals that companies spend 197 days on average to spot a breach caused by a malicious attacker. That means an intruder has had access to company data for over six months! Once discovered, it takes another 69 days on average to contain and remediate the issue. Why does this take so long?! Basically, most security and IT teams act in silos using different toolsets. They also have different priorities. The teams communicate inefficiently via spreadsheets or emails, leading to another loss of 12 days in coordinating teams for every vulnerability patch. When security teams finally determine what’s needed to fix a problem such as system patch, more time is lost in remediating the issue.

ServiceNow’s solution for Vulnerability Management
Vulnerability Response from ServiceNow can help you solve the issues above. It offers the following features:
- Integrates with market-leading vulnerability scanners and National Vulnerability Database
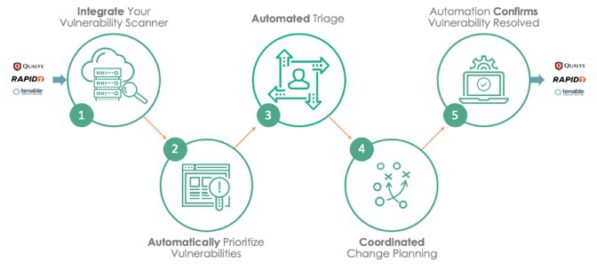
ServiceNow offers out-of-the-box integrations with market-leading vulnerability scanners like Qualys, Rapid 7, Tenable, etc. to import vulnerabilities and related CI information to the instance. All published vulnerabilities from NVD are imported and matched to the CIs in the CMDB, which will expose any vulnerabilities.
- Prioritizes vulnerable items using asset context and exploit enrichment
Most organizations must deal with tens or even hundreds of thousands of vulnerabilities. That means prioritization is crucial. In addition to the CVSS score, a standard score for vulnerabilities, and the asset criticality that we’re able to bring through integration with the CMDB and business services, exploit enrichment is another form of context to help identify and prioritize critical vulnerabilities. You can configure your own vulnerability calculator to define the exact customized risk score.
- Automates patch requests
When critical vulnerabilities are found, an emergency response workflow is automatically initiated that notifies stakeholders and creates a high-priority patch request for IT. Once the patch task has been completed, a follow-up scan of your vulnerability management system is initiated to confirm the fix. This results in a coordinated remediation strategy for vulnerabilities with the added benefit of visibility across teams.
- Populates and updates the CMDB through scan data
Many organizations don’t have an up-to-date and reliable CMDB. Using Vulnerability Response, you can import and update CI information to your CMDB as well.
- Seamless integration with other ServiceNow features
Since Vulnerability Response is part of the ServiceNow platform, it easily communicates with and harnesses the power of other applications and modules such as Change Management (to install patches), Incident Management, workflows, SLAs, and many more.
- Faster remediation thanks to orchestration
Employing orchestration tools allows you to further reduce the amount of time spent on basic tasks. ServiceNow leverages several programs and services to automate steps in the vulnerability remediation process, like installing patches or changing the network configuration.
Put your security first
Stop inefficient management of vulnerabilities and put your security first. Security tool integration and vulnerability automation and prioritization are the main drivers of ServiceNow’s Vulnerability Response, allowing for effective vulnerability management. The overall benefits? A more secure company and more time and resources to spend on value-adding (security) activities.
___________________________________________________
[i] Source: Ponemon Institute, Today’s State of Vulnerability Response & Cost of a Data Breach, 2018
Join 1400+ ServiceNow professionals
Sign up to our monthly Flow@Work Exclusive newsletter to get free access to our expertise and lots of tips and tricks to make work flow on the Now® Platform.



 Carel Jansen
Carel Jansen