Why you shouldn’t use ServiceNow ITSM to manage your security incidents

Lately, we encounter more and more organizations who require a solution for security incident management. In most cases, organizations use multiple tooling to manage their processes. Some of these organizations, when realizing the benefits of ServiceNow ITSM, start to think: why not utilize ServiceNow ITSM to govern our security incident process as well? They wonder if the Incident Management module would suit this need and whether it is comprehensive enough to be used in security-related incidents. In this blog, we will explain why this is not the best idea! We believe a tool, plus a well-defined process, is a valid need, but one that needs to be addressed properly.
Quickly jump to:
ITSM & Security definitions
The definition of security incidents is different from normal incidents. For normal incidents, we address CI/service availability. But when it comes to security incidents, the main goal is to manage the affected confidentiality and integrity aspects of a CI, asset or service. Let’s assume that one of the company servers is infected by a virus or hacked. The first step after analysis is to contain the incident scope, so it won’t spread to all other servers and affect the whole network or contain/remove the hacker’s access to the servers. In this security case, the first urgent action would be disconnecting the server and stop the service ASAP, which is completely different from the main goal of ITSM incident management. Because the costs of losing confidentiality or integrity would be higher than that of service unavailability.
Security stats prove the urgency
How many days do you think it would take to identify a security breach? 191 days. And how many to contain a security breach? 66 days. So, 257 days to find and contain a security breach? That’s unacceptable! Because the average costs of a data breach is $3.62M! These costs are calculated based on the Mean Time To Identify (MTTI) a data breach: $2.8M if MTTI <100 days and $3.83M if MTTI >100 days.
The way security is often organized
On average, an organization has 70+ security tools. And they have some processes in place. But what’s the problem then? What’s missing? Often, enterprise security tools are in disconnected silos and the number of notifications, events and incidents generated by security tools is too much to be handled without automation. And current processes are neither automated nor mature.
In today’s world, managing the overwhelming number of security incidents along with new innovative types of attacks requires a specialized tool and process developed for this particular purpose. ServiceNow understands this need and has launched an exciting SecOps package containing three main applications: Security Incident Response (SIR), Vulnerability Response (VR) and Threat Intelligence (TI).
ServiceNow Security Incident Response (SIR)
Let’s find out how SIR is different from ServiceNow ITSM incident management. For SIR, the first and main goal is containment and eradication, and not restoring the service as with ITSM incident management. In order to comply with these specific requirements, the ServiceNow SIR process uses either one of the two world-wide accepted security references: NIST or SANS. The default SIR process is based on the NIST approach, which has the following steps: Detect – Analysis – Contain – Eradicate – Recovery – Review – Closed.
Since security incident information is confidential data, SIR is a scoped application that has its own roles. Even the System Admin role doesn’t have access to security incident records. The application also automatically prioritizes incidents based on business impact (see Figure 1). Besides manual security incident creation, incidents can be automatically generated through integrations with security products like SIEM tools, firewalls, IDSs, antivirus programs, etc. Furthermore, incident information can be enriched using threat intelligence and all user-reported email attacks can be remediated quickly using the End-to-End Phishing Response function.
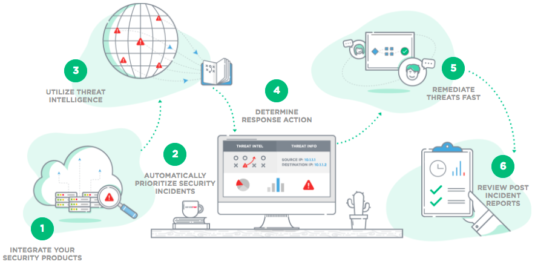
Figure 1. ServiceNow Security Incident Response
Different types of SIR workflows
There are many types of security incidents and it would not be possible to manage all of those using the same process. So, there are predefined workflows in SIR that facilitate collaboration per incident type, like confidential data exposure, denial of service, malicious software, lost equipment, phishing, policy violation, spam, unauthorized access, web defacement, etc. Based on the type of incident, the related workflow and unique SLA will be triggered and attached.
Conclusion
You simply cannot use ServiceNow ITSM incident management to manage your security incidents. It just does not suffice. Security incident management requires a totally different approach.
_________________________________________________________________
[i] https://securityintelligence.com/media/2017-ponemon-institute-cost-of-a-data-breach-study/

Join 1400+ ServiceNow professionals
Sign up to our monthly Flow@Work Exclusive newsletter to get free access to our expertise and lots of tips and tricks to make work flow on the Now® Platform.





